The ability for someone to hack into a medical device, like a pacemaker, is a scary thought. Not only do people want protection, but the FDA now requires it. Mike Kijewski, CEO, started MedCrypt to make it easier for medical device manufacturers to implement the necessary security features with just a few lines of code. PM360 spoke with Kijewski about what makes MedCrypt different from other cybersecurity companies and how cybersecurity can actually be a marketing advantage.

PM360: Why did you found this company?
Mike Kijewski: In 2014, I was working as a product manager at a medical device company and was pleasantly surprised to see a healthcare technology company deploying cloud-hosting applications such as Amazon Web Services (AWS) and Microsoft Azure. But when I looked at the area of cybersecurity in healthcare, specifically in medical devices, I saw they were spending a lot of time on fundamental software development around cybersecurity. I thought their focus should remain on building lifesaving technologies and saw an opportunity to make it quick and easy for them to implement core security features.
How would you describe the current state of cybersecurity in medical devices?
A lot of hyperbolic language is out there about how horrible the state of medical device cybersecurity is, but we don’t think that’s true. We think medical device vendors have been making lots of progress over the last few years and we have yet to see a case where the cybersecurity of a device outweighs its clinical benefit. Secure by design takes into account that more than ever—devices are going home with patients and operating outside of the hospital, which unfortunately is not part of the existing regulatory environment for medical device operation.
The FDA has stressed the importance of collaboration between healthcare delivery organizations (HDOs), medical device manufacturers, and security researchers in tackling cybersecurity requirements in medical devices. In October 2018, the premarket cybersecurity guidance mandated devices be designed securely to receive a 510(k) clearance.
What kind of cybersecurity features does MedCrypt offer?
We facilitate features that most medical device vendors agree should be in place, such as data encryption on the device, putting cryptographic signatures on data so you can verify nobody has tampered with it, and monitoring the behavior of devices and then applying software patches for vulnerabilities that are found out in the field. But one of the things that makes us unique: A healthcare-specific approach to cybersecurity.
Other companies build cybersecurity for Internet of Things devices like a thermostat and they think the same cybersecurity could work for a pacemaker since it runs the same processor and software. We’ve seen where patient safety is put at risk because of this, like when a patient’s heart procedure was interrupted because of an anti-virus scan. We believe, however, that a pacemaker is more like a CT scanner in terms of its regulatory requirements, so we built our product to work in almost any medical device.
On your website, it mentions how companies can use cybersecurity features as a competitive differentiator. So, what can you provide to create an advantage for medical devices?
That’s actually a controversial point among medical device vendors. Most believe that since everybody in the industry suffers if a patient is harmed due to a cybersecurity breach, it isn’t a good idea to market around your cybersecurity abilities.
To a large extent I agree with that. But some of the biggest challenges medical device vendors face today around cybersecurity are the risk of recalls from the FDA if a vulnerability is found and selling to hospitals concerned about cybersecurity. We’ve heard that answering questions from hospital administrators about a device’s security can double the length of the sales cycle. So any medical device company that takes a comprehensive approach to cybersecurity would ideally have a lower probability of recalls related to cybersecurity and a much easier time selling to hospitals.
What happens if your company actually detects a vulnerability? How do you prevent people from hacking a device?
I want to make sure that we’re precise about the language. A vulnerability is a flaw in the software that would make it possible for somebody to hack the device. Meanwhile, an exploit is when a hacker actually exploits a vulnerability.
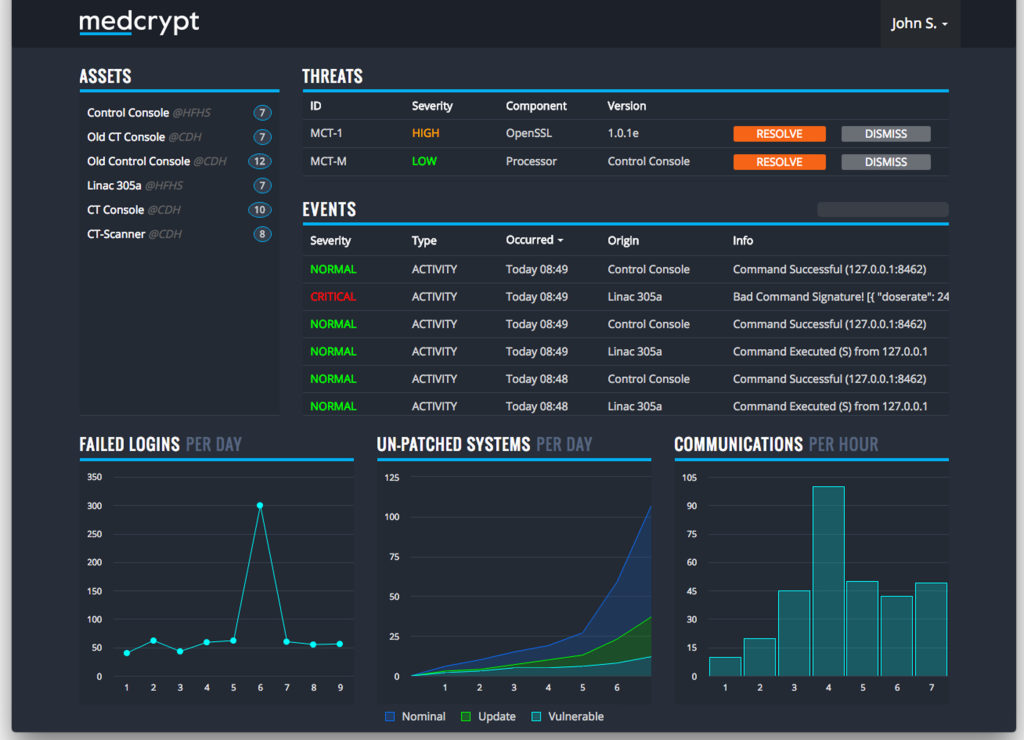
In terms of proactively managing vulnerabilities, we monitor the software library on a device to see if there are known vulnerabilities, notify medical device vendors when there is a vulnerability, and help them decide if it makes sense to patch that vulnerability. For exploits, we monitor what devices are doing out in the field, and if we spot abnormal behavior then we alert the medical device vendor who would have the ability to either escalate that to the hospital or confirm it is just one of their engineers testing something.
Are there any cybersecurity features you don’t currently offer but would like to in the future?
We have grand long-term plans for both the product we’re offering and the company itself. While I can think of lots of areas where we would like to expand, one obvious one is inter-device security. Today, the FDA is focused on intra-device security, the security of a particular device and the core functions of that particular device. But these devices are also typically designed to communicate with another vendor’s product.
For instance, a drug infusion pump made by Vendor A can talk to an electronic medical record system made by Vendor B. The protocols used to help these devices communicate are usually managed by a hospital and you can configure these protocols in lots of different ways—some of which are more secure than others. Down the road we plan to help medical device vendors and hospitals ensure that these devices are communicating with one another more securely.